The TL;DR
- Cybercrime group ShinyHunters impersonates trusted parties to trick people
- They urgently request access or a configuration change
- This post shares their playbook and your prevention checklist
- Scroll down for a free, <2-minute video briefing that you can use to arm your people
In this post, we’ll cover the threat posed by ShinyHunters, the cybercrime group behind several recent attacks. We’ll share how they operate and how your people can spot them.
The threat
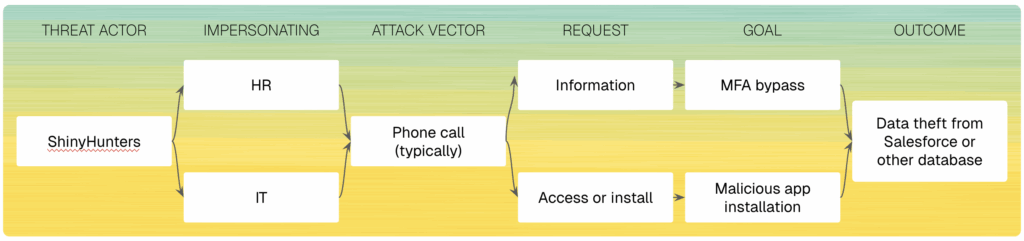
ShinyHunters is a cybercrime group known for breaching high-profile organizations and selling their stolen customer data on the dark web. They’ve been linked to breaches at companies like Ticketmaster, Santander, and Google by exploiting CRM systems like Salesforce and Workday. Their calling card: sophisticated social engineering paired with opportunistic targeting of big datasets.
Targeted cohorts
The best targets for ShinyHunters are people with access to databases of people, ideally customers. Key targeted cohorts include employees with access to Salesforce or another CRM.
Their playbook
ShinyHunters reaches out to your employees from basic data available, such as names, titles, emails, and phone numbers. They impersonate a trusted person from HR, IT, payroll, or vendors and make an urgent request or pretext (e.g., “We need this right away”), often using escalating commitment to gain just one extra detail or one configuration tweak.
How to prevent
Urge your people to be vigilant about urgent requests, even from known people, and not to take chances. Specifically, they should:
- Not share passwords, MFA codes, or other sensitive information by phone, text, or email.
- Not make system configuration changes when asked to do so remotely.
- Verify requests like this through a trusted channel, or ideally, establish a verification process ahead of time.
How to contain and remediate
If your people do fall victim (entirely or part-way), they should:
- Stop interacting (hang up, stop texting)
- Alert security
- Save message or capture screenshots
- Block caller or sender
And you should:
- Review call logs, if applicable
- Notify impacted parties (customers, employees, vendors)
- Trace the entry point (CRM, etc.)
- Monitor for suspicious activity or account compromise
- Update policies
- Deliver targeted employee interventions to avoid repeat incident
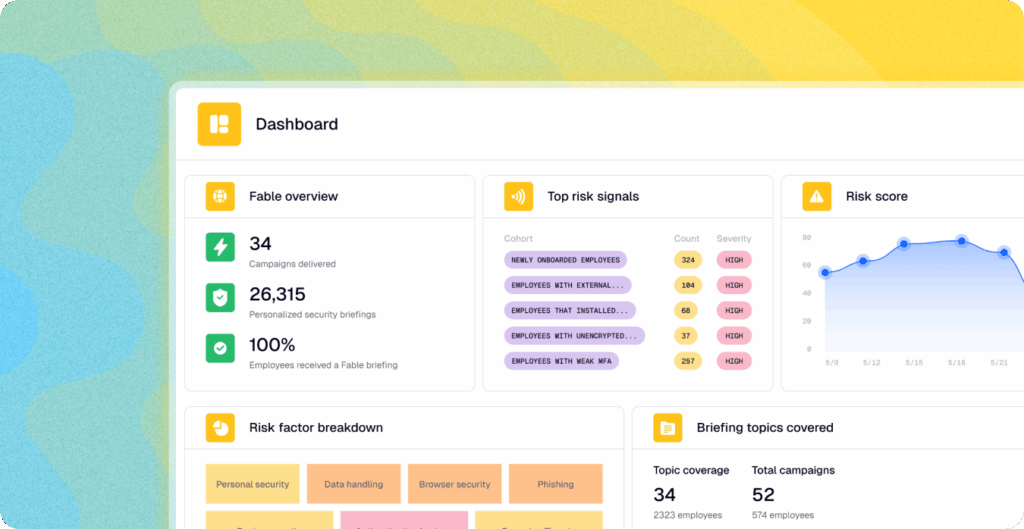
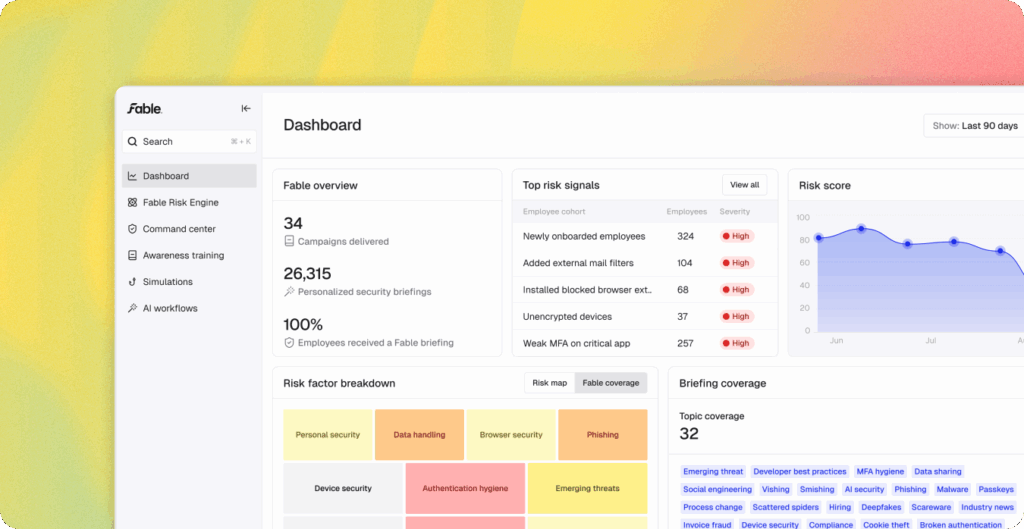
How Fable can help
Here’s a short, highly-specific video briefing you can download for free and share with your employees.
If you’d like risk-based briefings and nudges that are hyper-targeted and customized to your organization, try the Fable platform.