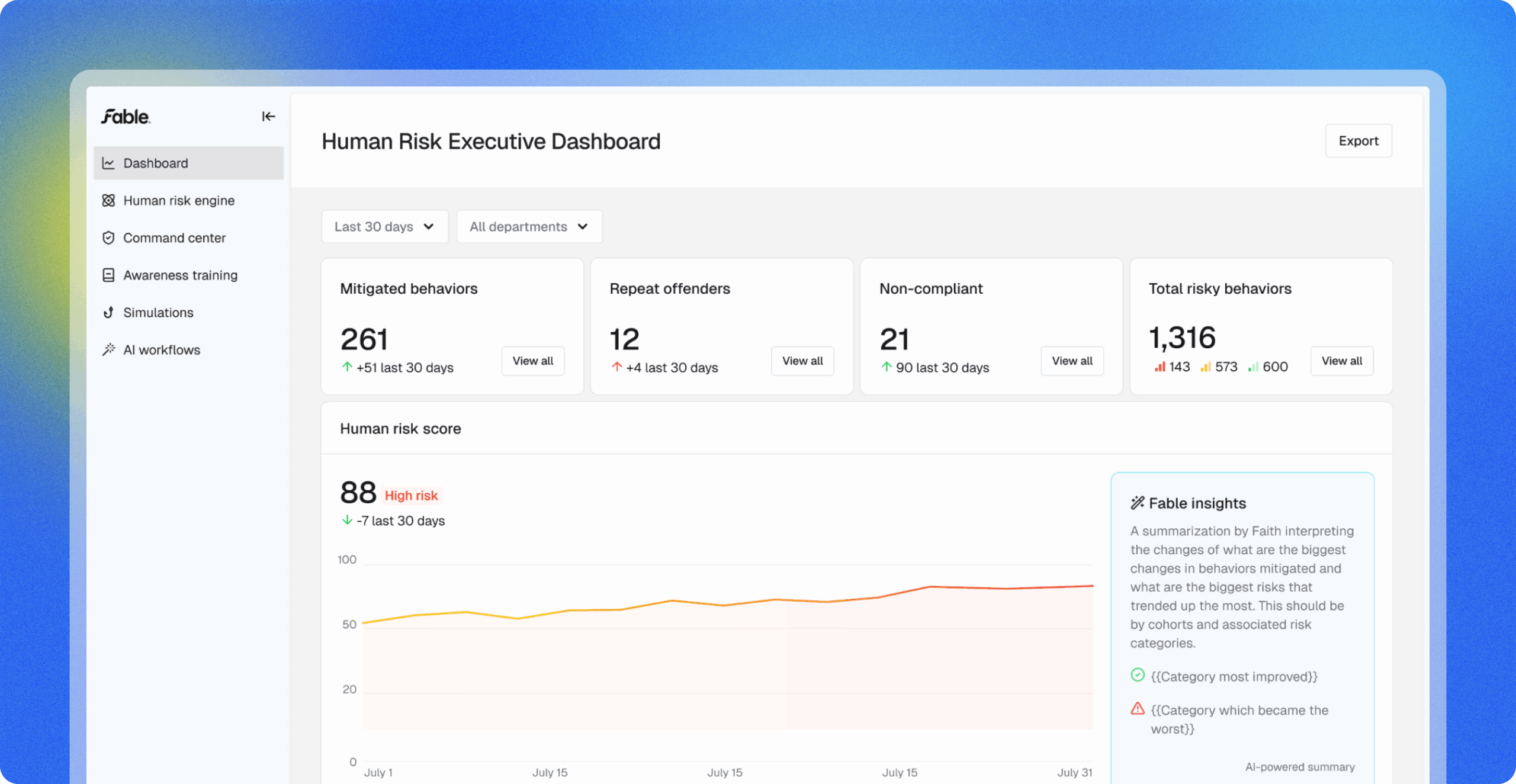
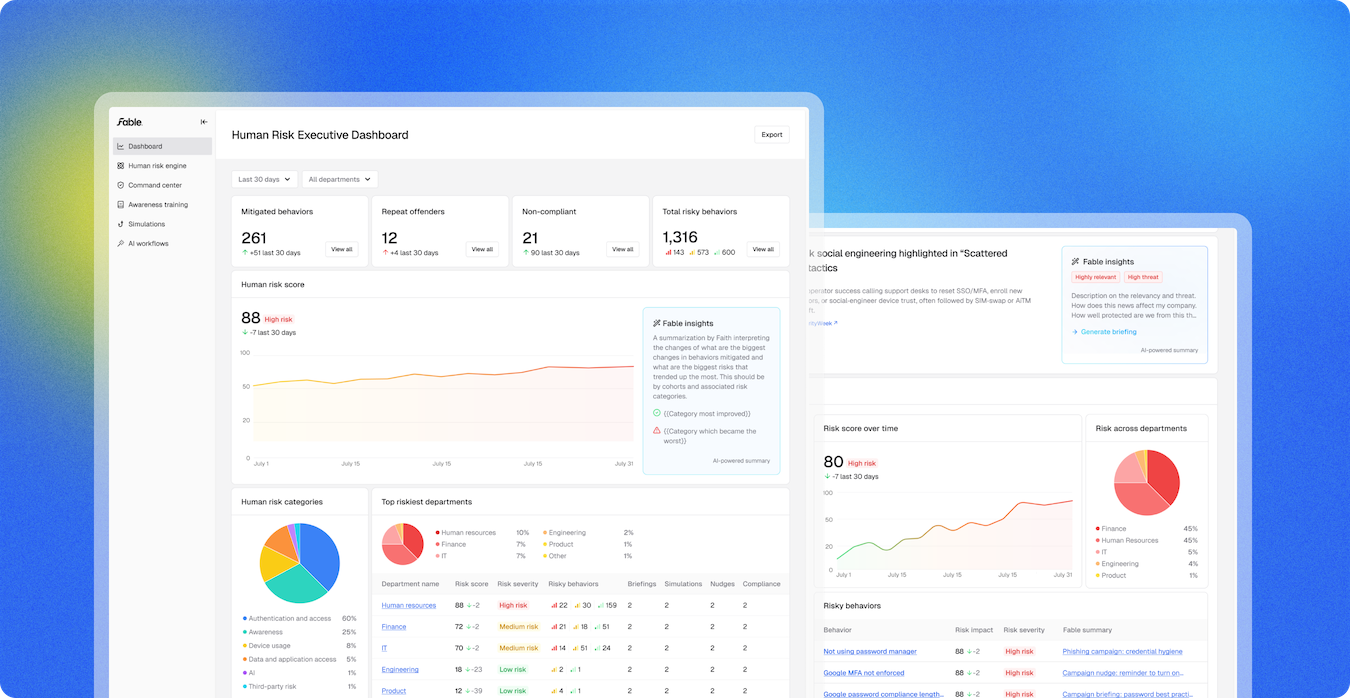
We just launched exec-ready human risk reporting—a new way to show executives and boards what really matters.
In this 15-minute* Fast Fables session, Fable CEO Nicole Jiang, CIO J.D. Whitlock of Dayton Children’s Hospital, and Chief Customer Officer Jamie Barnett reveal how to move beyond clicks and completions with clear, explainable metrics that quantify your true human risk. See how organizations can benchmark performance, pinpoint high-risk behaviors, and take fast, targeted action with Fable’s new executive dashboard and AI-powered insights.
Yes, it’s really 15 minutes. No fluff—just the good stuff. Watch the recording above.
FAQs
1. You mentioned interventions. How do those work?
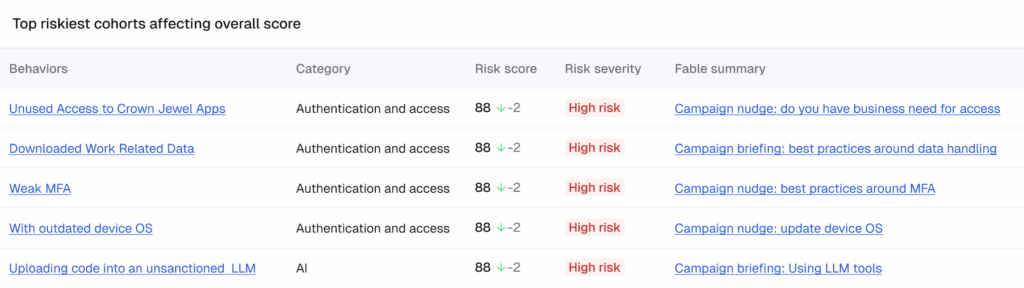
In Fable, you can drill down from the risk score to the risk factors, and from there, to the specific behaviors driving that score. For insecure behaviors, Fable recommends a targeted intervention, such as a short video briefing or nudge, which can be delivered to the affected cohort. Interventions run like training or phishing campaigns, with full performance tracking: engagement, completion, and actions taken (e.g., OS updates, MFA adoption, or corrected data sharing).
2. Does this require deep integrations to get started?
Not at all. Fable offers multiple paths to value depending on your setup. You can launch quickly with minimal configuration, like uploading a user list, to run phishing simulations and awareness campaigns, even on timely or targeted topics. Integrations unlock deeper insight and automation, but they’re optional to start seeing impact.
3. How hard is it to get this kind of reporting if our data is fragmented across different tools?
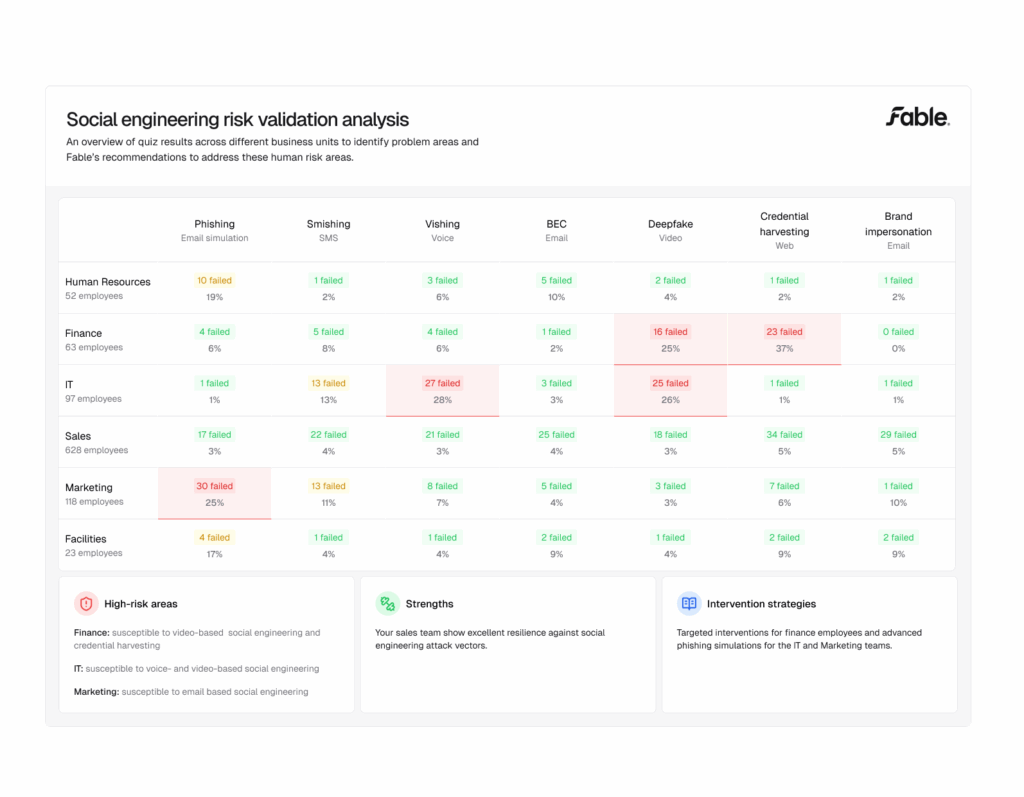
That’s where most teams begin. Fable can generate meaningful insights even from partial datasets, then progressively enrich reporting as integrations expand. You don’t need a perfect data landscape to start identifying risk patterns.
4. What makes up the risk score?
The risk score combines multiple factors—such as authentication hygiene, device security, and data handling—each tied to measurable user behaviors. You can drill down to see which specific habits (like weak MFA or unsafe file sharing) contribute to each factor, providing transparency into the “why” behind the score.