The TL;DR
- Self-service SSO: Fast setup, simple login, strong security
- Realistic phishing simulation: Add .docx attachments and filter bot clicks
- Campaign efficiency: Preview, edit, and complete campaigns with ease
This release is about quality results and efficiency of use. The following is now live in your tenant. Here’s what’s new and how to get started.
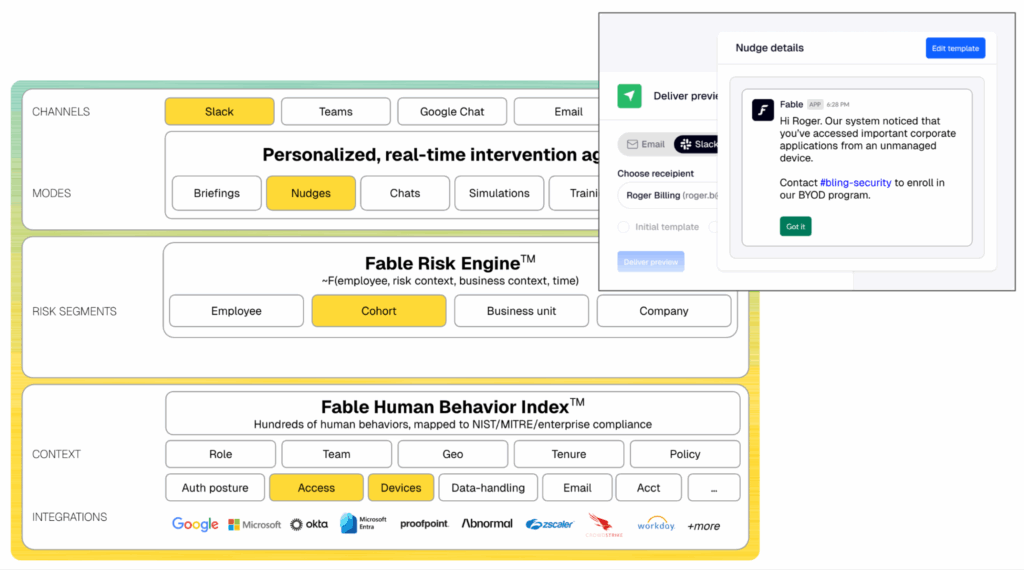
Self-service SSO
Set up SAML SSO intuitively and let people authenticate with their directory and/or log into Fable with their email address. This makes for a fast setup, frictionless login, and strong security.
- How it works: settings → integrations → SAML SSO.
- Limitations: Each tenant supports one SSO configuration.
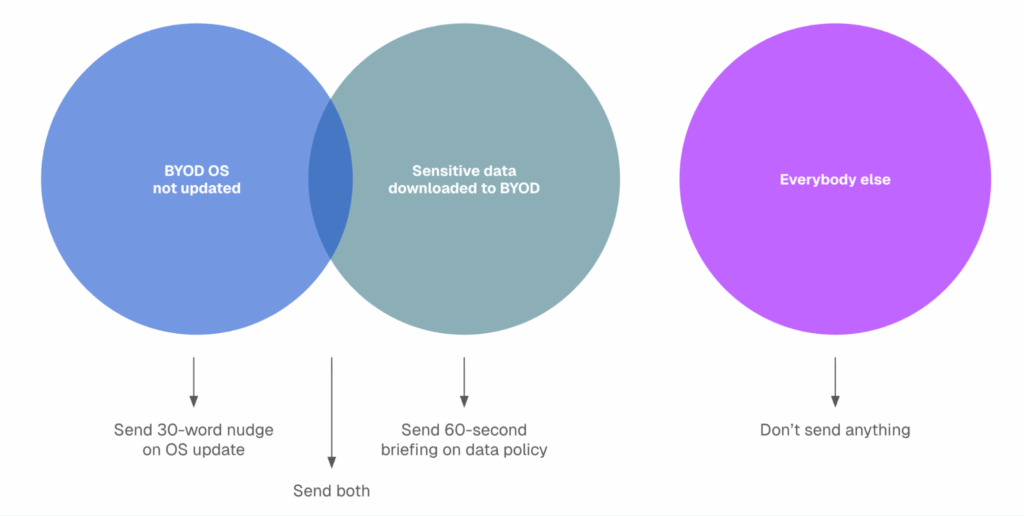
Accurate phishing results
Stand behind your phishing results with confidence. We automatically clean up results by filtering bot clicks from simulation results, self-tune the system, and enable exceptions.
- How it works:
- Filter bots: simulations → reporting → filter false positives → select IP range or ASN name from pull-down.
- Limitations: Currently limited to .docx attachments only; filtering depends on the accuracy of input signals.
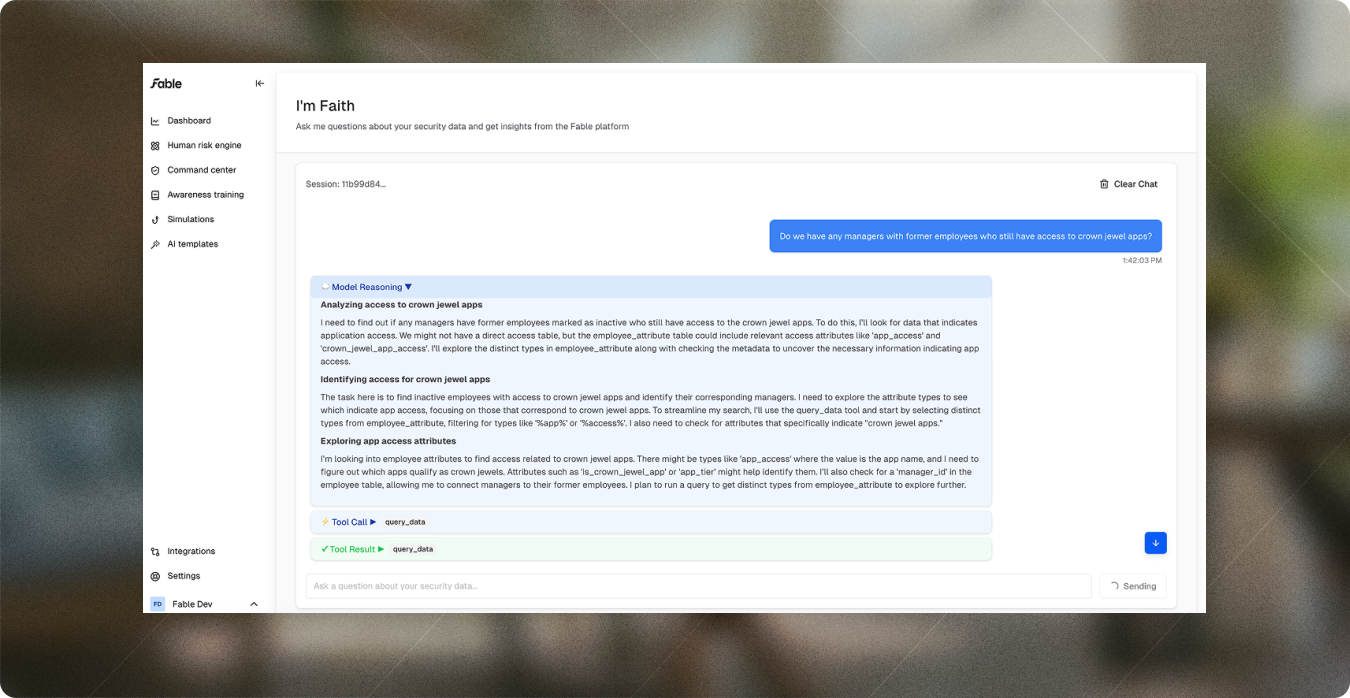
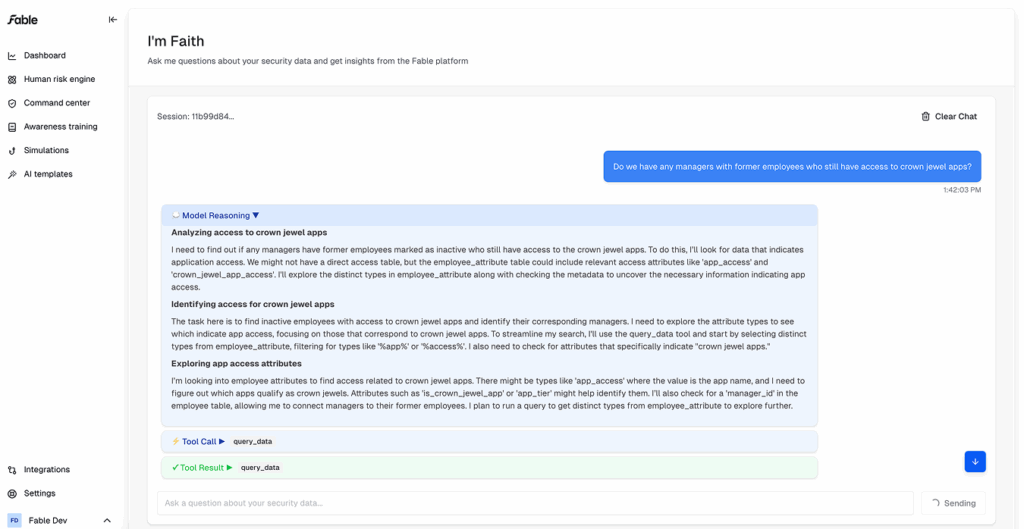
Campaign efficiency
Manage campaigns faster and achieve more customization with briefing template updates, campaign previews, campaign-level editing, the ability to upload employee names pre-integration; and the ability to mark campaigns as complete.
- How it works:
- Preview campaign: AI templates → click into a campaign → preview → select multiple preview recipients.
- Edit at campaign level: Command center → click into a campaign → templates → click to edit for campaign-level emails without changing global defaults.
- Upload employee names:
- Mark complete: Command center → ellipses next to campaign → mark campaign as complete.
- Limitations: Previews capped at 10 recipients; marking a campaign complete is irreversible.
Cybersecurity quiz
Test employees’ cybersecurity awareness and ability to detect deepfakes with a 10-question quiz.
- How it works:
- Awareness training → active trainings → select Cybersecurity Awareness Month.
- ALSO available decoupled from the Fable platform for use by non-customers or customers pre-integration.
- Limitations: Reach out to Fable for help customizing deepfakes.