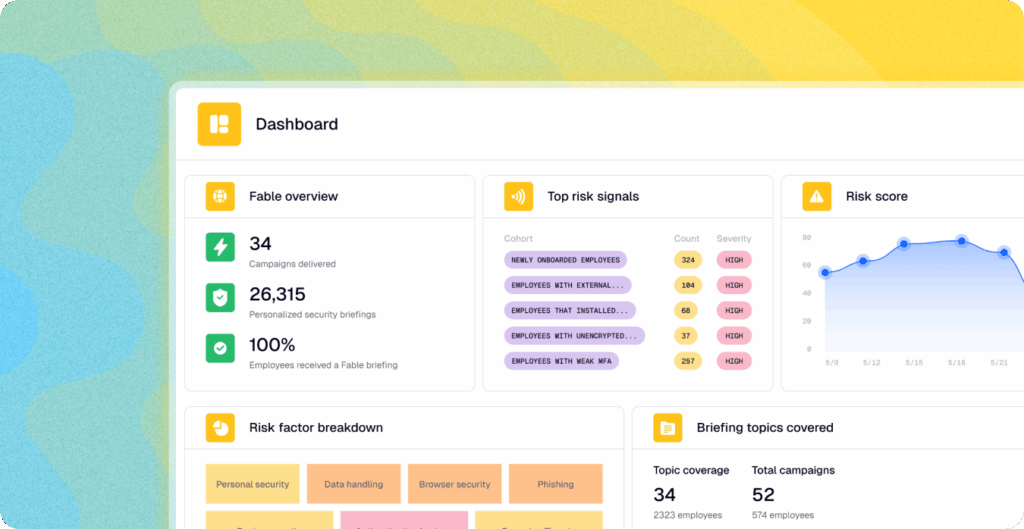
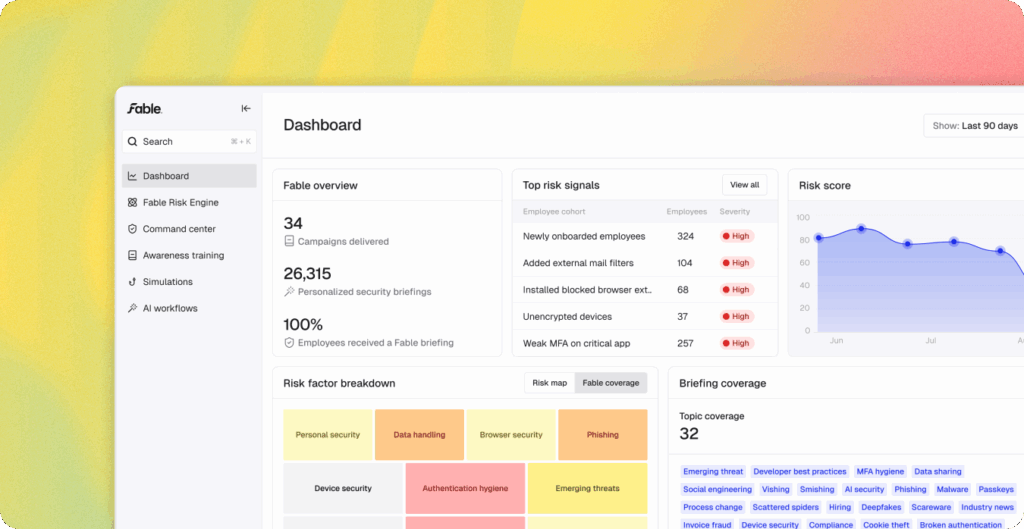
Day 2 of 12 days of riskmas (or, if you prefer, risk-mukah or the non-denominational risk-ivus)
The TL;DR
- Security teams see countless risky behaviors
- These ten human risks show up everywhere
- Top risks range from weak credentials to social engineering
- Targeting these risks with precise interventions is key to reducing exposure
- Download the full report for metrics, real-world examples, and insights to strengthen your human risk strategy for 2026
Security teams use Fable to achieve objectives ranging from raising general awareness to raising awareness for targeted groups to shaping specific behaviors to reduce risk. Below, we group these campaigns by type and goal and place them on a maturity map aligned with integration depth and targeting level.
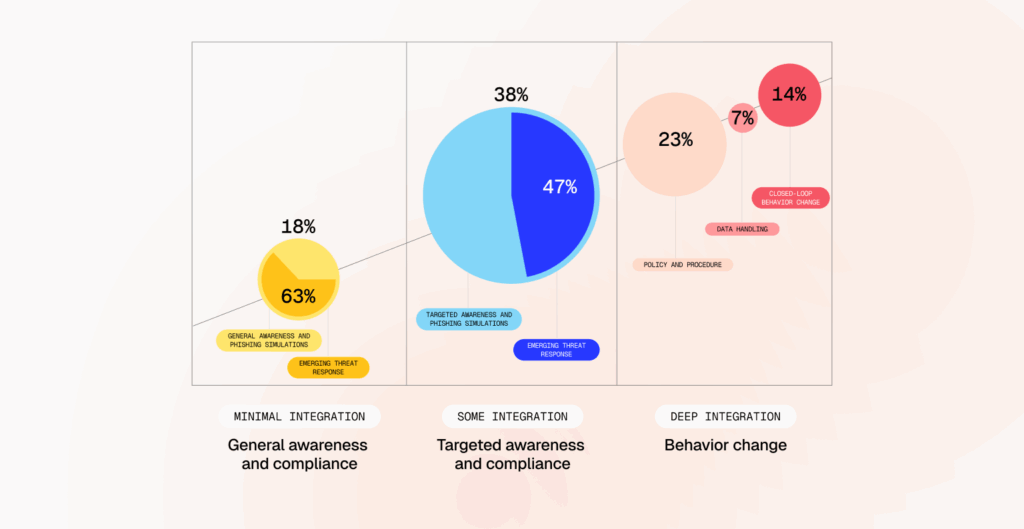
Nearly one-in-five (18%) campaigns are in the first stage of maturity: general compliance. This consists of broad-based phishing simulations and awareness training sent to everyone in the organization. Despite being “one-size-fits-all,” a full 63% of them are targeted in a way: they’re focused on a specific emerging threat. That could range from a new ransomware campaign in a hospital to a spate of CEO impersonation vishes making the rounds in a bank to a malware threat circulating on WhatsApp. Depending on how fast-moving the threat is, you may need to get ahead of it and respond within hours, not days or weeks.
38% of campaigns are in the second stage of maturity: targeted compliance. These customers have integrated their directory or workspace platform such as Google Workspace or Microsoft 365. They are largely targeting campaigns to cohorts (groups of people of the same affinity group or exhibiting the same security behavior) based on role, access, or risk. Of those, 47% are in response to an emerging threat, such as ShinyHunters scammers targeting customer database administrators.
44% of campaigns are in the third stage of maturity: behavior change. These are campaigns where the customer has integrated Fable more deeply into their technology stack—such as with single sign-on like Okta, enterprise browser like Google, SASE like Netskope, and endpoint detection and response like CrowdStrike. They’re running highly-targeted campaigns to shape behavior, such as prompting employees not to upload sensitive content to unsanctioned generative AI, rotate credentials when they’ve been exposed in a breach, and comply with security protocols such as enabling multi-factor authentication or adopting a password manager. 32% of this category, or 14% of the total, actually verify employee behavior change in a closed-loop way.
Most—but not all—of our customers start simply and run a few general compliance campaigns to get started. This may be because they need to cover the basics from the human risk product they replaced. While broad-based campaigns check the compliance box, they rarely drive meaningful behavior change or reduce risk. So, we encourage our customers to explore how they can target their campaigns for maximum impact.
Be sure to check in tomorrow (day 3) as we explore the differences between general and targeted campaigns—and measure the difference in outcomes between the two.